SQHell
Room Link: https://tryhackme.com/room/sqhell
Put in SQL Injection notes
https://pencer.io/ctf/ctf-thm-sqhell/#flag-4---out-of-band---browser-method
Scans
Initial scan
Kali
nmap -A $VICTIM
Longer scan
Kali

TCP/80 - HTTP
Kali

Flag 1


List

Flag 2

Blind/Time - Curl Method
This command gets the page right away
Kali
Changing the 86 to 84 there is a delay of 5 seconds.
Kali
flag.py
Kali

Flag 3 - Blind/Boolean - Curl Method
SQL Injection Info
Looking at the room description we’re told specifically to find five different flags using various types SQL injection:
There are a ton of great resources out there on the internet to help with SQLi. A few good ones that have helped me are this, and this, which both have lots of information and examples. There’s also this cheatsheet which is nicely laid out, and this one which has a good list of boolean based examples to try. Finally this article is a good introduction to the five basic type of SQL injection.
In real life we need to use different tools depending on the scenario. So for this room I’m going to cover the flags using some or all of these methods for each:
For BurpSuite I’m using FoxyProxy to redirect my browser to it. Here’s the config needed in case you haven’t got it set up:

Initial Access
First let’s add the server IP to our hosts file:
Now we can have a look at the website:
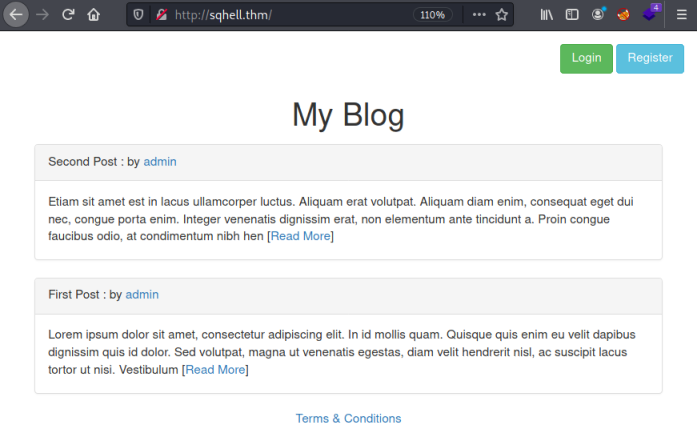
We have a simple static html based website with five areas for us to exploit. Let’s start on the first flag.
Flag 1 - In-Band/Error Based - Browser Method
The first flag is the easiest, start by clicking on the Login button which takes us here:

We have username and password boxes, it’s safe to assume we’ll be doing a simple sql injection authentication bypass technique here.
I tried a few different ones from the cheatsheet mentioned above, this was the one that worked for me:
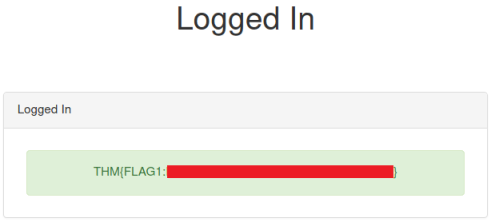
Simply enter that in the Username field and press Login:

We are taken to another page which reveals the first flag:
Flag 1 - In-Band/Error Based - Curl MethodPermalink
We can also do this using curl, with the same authentication bypass technique. To automate the process of finding which one works I copied the examples from the cheatsheet here to a file:
Then used a simple loop in BASH to read each line and try it against the website:
As you can see quite a few different ones worked.
Flag 1 - In-Band/Error Based - Burp MethodPermalink
We can use Burp to intercept the browser request. First make sure you have FoxyProxy on and set to use Burp, then use anything for the username:

With Intercept set to On in Burp, when you click the Login button in your browser it gets redirected and caught:

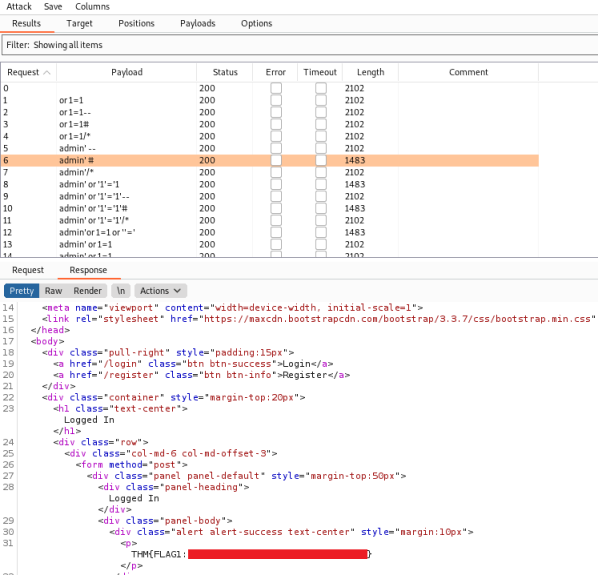
Right click anywhere on the text and chose Send to Intruder. Check the last line has something within $ set against the username field, this is the variable that Burp will replace with our word list:

Switch to the Payloads tab and load a list of bypass techniques to try. I used the same file I’d copied them in to for the above curl method:

Click the Start Attack button and wait for burp to try everything from your list. Looking at the results you’ll see a few lines with a smaller length to the others. If you switch to the response tab you can see these are the responses containing our flag:
Flag 1 - In-Band/Error Based - SQLMap MethodPermalink
The last method to look at is arguably the easiest. Once you know how to use SQLMap it makes the process of discovery and enumeration much easier. If we pretend we don’t know the login page is vulnerable then let’s follow the process we could use to exploit the page. This is a useful post on using SQLMap for SQLi.
First we run an initial scan to see what SQLMap can discover about the database behind the logon page:
There’s a lot of information, the key point is:
With the information gathered we can tell SQLMap to use the username and password fields, set the database to mysql, and dump the databases it can find:
Again, a lot of information but the important part is the database it found:
Next we can ask SQLMap to dump the contents of that database:
With the password found for the admin user we can either login in via the browser or use curl again to get the flag:
Ok, that was four different ways to get flag 1. Let’s move on to the next flag.
Flag 5 - In-Band/Union - Browser MethodPermalink
The next easiest flag is number five. For this one we’ll be using parameter tampering and a UNION based exploit. I did another TryHackMe room called Jurassic Park where I used the same techniques as follows, you can see that post here.. There’s also helpful articles here and here that are worth a read.
First let’s see what we have:

We’re looking at one of the posts and can see it has a parameter on the end of the URL, in this case it’s ID=1. There’s lots of ways to check if this is vulnerable, probably the easiest is to add a ‘ on the end:
 ]
]
It says there’s an error in our syntax, which tells us our extra character on the end wasn’t removed. We could also do something simple like AND 1=1:

As before we can see the statement was evaluated with our extra part on the end. In this instance AND 1=1 is true so the page appears as normal. Now we know it’s vulnerable we can start to dig deeper.
First we want to know how many columns are in the table. We start at 1 and add columns until we get an error:

So here I did ORDER BY 1 then ORDER BY 1,2 and so on until I got to 5. The error at that point tells us there are four columns. Next we want to see which of those columns are useable:

The UNION ALL statement is used to show us which column appears where on the page. We want the output to be visible, otherwise we won’t be able to see the data we retrieve. We can see column three is the main section of the page, so plenty of room for our output. We’ll use that one for all our subsequent commands.
Let’s get the database name:

Now we want the tables in the database:

Finally we see the tables in the database, flag sounds like the one we’re looking for. Let’s have a look at the contents of it:
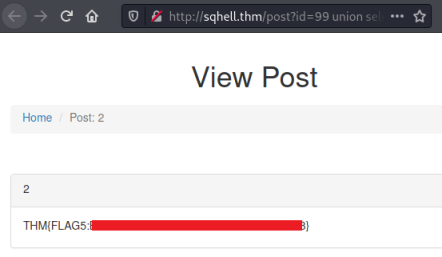
We have the flag. Let’s move on to a different method.
Flag 5 - In-Band/Union - Curl MethodPermalink
I went in to detail on the last flag on using curl instead of the browser. If you can use a browser you would because it’s easier, but in case it’s not possible here’s how to do this flag using curl.
First check how many columns we have:
We have four columns, as before we check to see which one is useable to display the data we retrieve:
I use grep to filter the output down to just the body of the response. We see column three is the one to use. Let’s find the database name:
Now find the tables in it:
Then get the flag from the table:
Flag 5 - In-Band/Union - SQLMap MethodPermalink
Moving on to SQLMap and like flag 1, this is pretty simple. First check for the post page parameter for vulnerability and find any databases:
As before, we’ve found the database is called sqhell_5, now dump everything:
We have the flag with only two runs of SQLMap, nice and simple!
Let’s move on to the next flag.
Flag 3 - Blind/Boolean - Browser MethodPermalink
I found this guide, which is a good in depth look at blind or boolean based attacks.
First looking at the Register page to see what we are dealing with:

If we try admin as the user we see a message saying it’s taken:

If we try test as the user we see a message saying it’s available:

Looking at the source code for the page we see how this works:
The script section calls a function called user-check to see if the name you’ve entered is available. We can visit this endpoint directly:

Here we see the JSON output showing us the username isn’t available. First we test for SQLi:
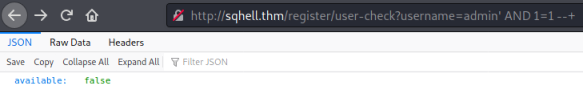
We still see available is false so we know we can perform SQLi and use the true/false response to confirm our query. Now we know this works our first task is to find the database name. We could continue in the browser, but for speed I’ll switch to curl.
Flag 3 - Blind/Boolean - Curl Method
Let’s test how many characters are in the database name:
Kali
This tells us the database name length isn’t 1 character long. Next we try two characters:

Kali
Same answer for two characters, so we continue adding one and testing until we get a false:

Same answer for two characters, so we continue adding one and testing until we get a false:
Kali

This tells us the length of the name of the database is eight characters. Now we want to find what those eight characters are, we can cheat a little as we can guess it’s in the same format as the previous flags. So with the knowledge that it is probably sqhell_3 let’s test the first character. To do this we need to know the ASCII code for lower case s, which is 115 known by looking at this handy table.
Let’s see if the first character is equal to s:
Kali

False tells us the letter isn’t available, or in other words there is a match. So we’ve confirmed the first character is s, let’s check for q. I also made this one liner to loop through all uncaptalize letters to make it easier.
Kali

I kept doing this until the last eighth character. Writing down the results to convert to ASCII
Kali
Link: https://onlinetools.com/ascii/convert-decimal-to-ascii

We’ve confirmed the database is called sqhell_3. Next we would use the same technique to get the table names in the database, of course that would be a long a laborious process. Used this script to get the flag.
flag.py
Kali

Flag 4
Out-of-band - Browser Method

We see her just like on the posts page there is a parameter. Let’s test to see if we can inject like before:

Adding AND 1=1 results in a true statement which proves we can inject here. Now we need to determine the number of columns in the table just like we did for flag 5. We do this the same way using the ORDER BY statement.
So just like before we start with ORDER BY 1, then ORDER BY 2, and so on until we get to ORDER BY 4 where we see an error:


Now we know how many columns we have we can use a UNION statement to test which ones are visible:

Here we’ve used a false ID, which would result in an error but instead we’ve used the UNION statement to retrieve the column numbers. Now we know column one and two are useable we can retrieve the user and database:

Next we want to see the tables in the database and can use the same query as before:
However this time when we ask for all tables using group_concat we only see the one user table:

We know a different database contains the posts table, but we find the expected flag table can’t be queried here. It’s at this point that we need to go back to the hint about running a query inside a query. And we again need to determine the number of columns:

Here I’ve just added an ORDER BY query to the end of the UNION SELECT 1, and enclosed it in quotes so it gets evaluated. As before we keep adding columns until we something changes:

We can see at five columns the posts disappear. This tells us there are four columns. Now we can use the same query as before to get the flag from the flag table:

Flag 5
In-Band/Union - Browser Method
The next easiest flag is number five. For this one we’ll be using parameter tampering and a UNION based exploit. I did another TryHackMe room called Jurassic Park where I used the same techniques as follows, you can see that post here.. There’s also helpful articles here and here that are worth a read.
First let’s see what we have:

We’re looking at one of the posts and can see it has a parameter on the end of the URL, in this case it’s ID=1. There’s lots of ways to check if this is vulnerable, probably the easiest is to add a ‘ on the end:

It says there’s an error in our syntax, which tells us our extra character on the end wasn’t removed. We could also do something simple like AND 1=1:

As before we can see the statement was evaluated with our extra part on the end. In this instance AND 1=1 is true so the page appears as normal. Now we know it’s vulnerable we can start to dig deeper.
First we want to know how many columns are in the table. We start at 1 and add columns until we get an error:

The UNION ALL statement is used to show us which column appears where on the page. We want the output to be visible, otherwise we won’t be able to see the data we retrieve. We can see column three is the main section of the page, so plenty of room for our output. We’ll use that one for all our subsequent commands.
Let’s get the database name:

Now we want the tables in the database:

Finally we see the tables in the database, flag sounds like the one we’re looking for. Let’s have a look at the contents of it:

Last updated